Like before, we can utilize "runas" to spawn a rdp session with our compromised DA account:
A key point prior to connecting to RDP, is to mount our C: drive of our attacking machine so that we can transfer files via our RDP protocol connection. When we receive our RDP prompt, we click on Options > Local Resources and "More..."
We then choose a drive that we want to use in our remote session. In our case, we use our Local Disk (C:):
Now, when we connect to our Domain Controller, we can see that our C:\ of our attacking machine (that is off network) has now been mapped.
We then spawn an administrative Command Prompt:
We verify we are the Domain Admin, on a Domain Controller and we check the path to NTDS:
As shown above, our DSA Working Directory and DSA Database file are located in C drive. With this information in hand, we need to create a shadow copy of the C drive.
With the Volume Shadow Copy created for C:\, we can copy out the ntds and the system hive file to a temp directory:
Now that we have our files copied. We need to transfer them out. We can copy them to the C:\ of our attacking machine that we mapped earlier during our RDP connection. We verify the path with net use:
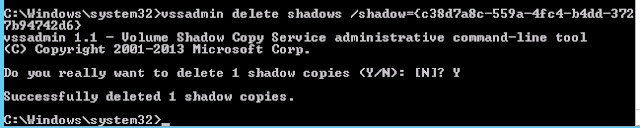
With our files exfiltrated, we need to cover our tracks. We delete the shadow copy, our copy of the ntds.dit file and copy of the system.hive file:
Now, with our files in hand, we can use Impacket's SecretsDump to locally extract the contents of the files.
And there we have it. An example of how we can pull the NTDS from a Domain Controller and extract its contents with SecretsDump. There's no right or wrong way to accomplish this, this was just one method that works.
Hope this was helpful.